I'm thrilled to have you explore my digital space where creativity meets functionality. Here, you'll find a curated collection of my projects, experiences, and the journey that has shaped my professional path. Dive in and discover the work that I am passionate about, the technologies I excel in, and the innovative solutions I've crafted. Whether you're here for collaboration, to hire, or just to satisfy your curiosity, I hope you find inspiration and insight. Thank you for stopping by, and I look forward to connecting with you!
Hello,
I'm Colin Kirkwood — a Computer Science graduate specializing in cybersecurity, software development, and applied mathematics. I’ve always been naturally curious — the kind of person who questions how and why systems work the way they do. That mindset has led me to approach cybersecurity not just as defense, but as investigation: uncovering how threats evolve, where data flows, and how to make complex systems more resilient.
My experience spans both engineering and intelligence domains. As a Security Engineering Intern at Tenable, I developed a web application that automated and streamlined customer data management through Google Apps Script, OAuth, and API integrations, improving visibility and workflow efficiency across teams. I also began research on secure image verification systems, exploring how cryptographic and metadata validation can be applied to media integrity — bridging creativity with security principles.
Previously, as a Threat Intelligence Engineer Intern at ThreatQuotient, I contributed to a large-scale community threat intel initiative. I performed CTI report validation, maintained platform utilities, and onboarded new users to the ThreatQ environment. Working hands-on with IOCs, OSINT feeds, and MITRE ATT&CK mapping, I gained a strong understanding of how actionable threat data supports incident response and SIEM-driven detection workflows.
Currently, I’m advancing my cloud security knowledge with AWS certifications (Cloud Practitioner, Solutions Architect Associate) while studying automation, incident response automation, and data enrichment for modern security operations. I stay engaged with emerging technologies through the Digital Asset Association, where I explore blockchain, cryptocurrency, and the evolving cybersecurity implications of decentralized systems.
With a solid foundation in threat intelligence, scripting, and cloud technologies — and a genuine drive to make security data meaningful — I’m eager to contribute to an organization where analytical rigor, automation, and innovation intersect.
Best regards,
Colin Kirkwood
Some cool projects:
- Self-hosting my own meta search engine using Searx and Docker
- Hosting and creating a dark web website on Tor
- Creating my own cyber deck with retropi custom controllers
- Using ultrasonic sensors to calculate distance displayed on an I2C LCD screen in micro-python/circuit-pytho
- Creating a bad USB to hack HID's on RPI0W and Pico.
- Setting up a minecraft server for friends
- Creating an image verification system using the Pi as the baseline device
Smart Contract Development/Web3:
- I created an inscription minter on a few testnetworks. This makes it possible to inscribe arbitrary data on the blockchain.
- Image to ASCII converter with result able to be minted as an ERC-721.
- ERC-20 Development (memes)
Some Web Development Projects:
- Frontend for image to ascii converter
- Shared paper on Money, Philosophy, energy and Cryptocurrency on my secondary website
- The web app I developed during my internship at Tenable
- The website we are currently on!
AI projects
- Colin's Curator is a chatbot here on this website in the bottom right corner. Ask it some questions about me or the role you are looking for.
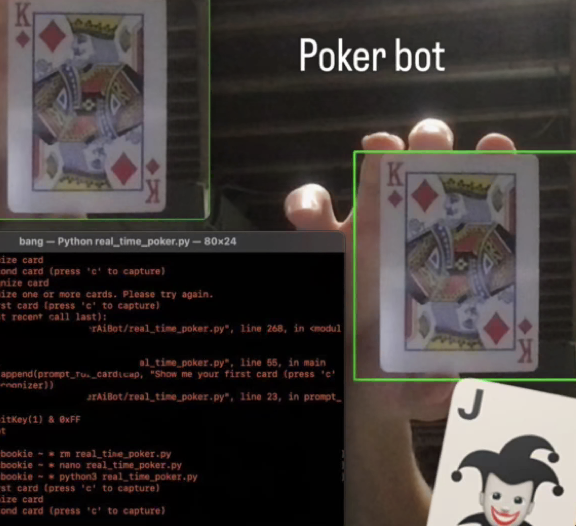
- Card recognition using treys for a poker bot
- Coral.ai google usb stick with the raspberry pi for image recognition testing
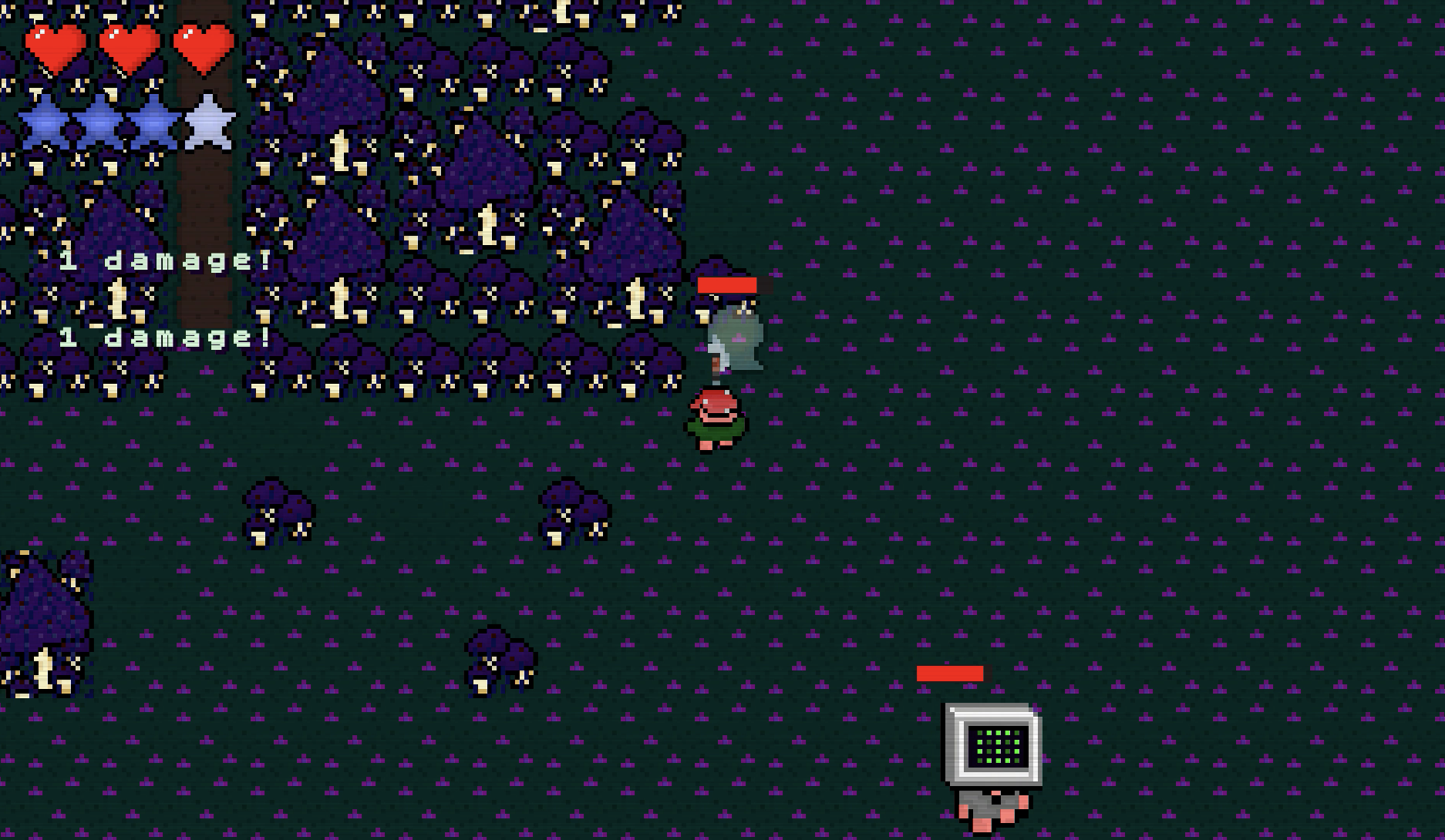
- A* pathfinding integration into my game FUNGUY
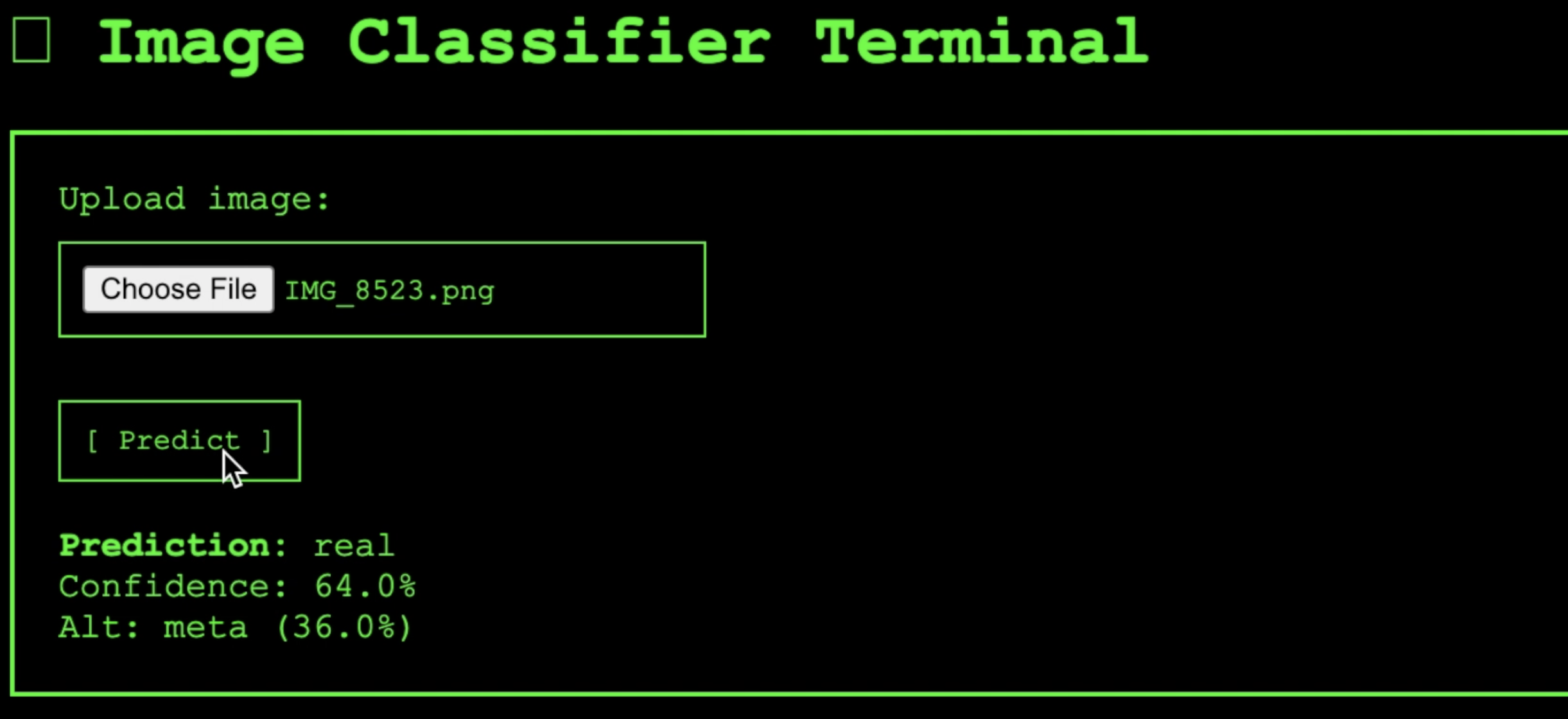
- Trained an AI model to recognize the difference between authentic images and images of other images (like: a photo of a dog on my laptop screen, a photo of the sunset in a magazine and more)
I recently completed a Security Engineering Internship at Tenable (Summer 2024), where I developed a web application using Google Apps Script, OAuth, and API integrations to streamline customer data management. This project, focused on enhancing post-sale support for the sales team, allowed me to merge technical skills with practical business needs. I was also given the opportunity to present my work at the QBR and final intern presentations which enhanced my communication skills.
Previously, I served as a Threat Intelligence Engineer Intern at ThreatQuotient (Summer 2023 – Spring 2024), where I trained on the ThreatQ Threat Intelligence Platform. My responsibilities included validating threat intelligence reports, maintaining platform utilities, and onboarding new members as part of a large-scale community project involving over 100 companies. This role deepened my understanding of cybersecurity in a collaborative environment, working with over 50 open-source intelligence sources, RSS feeds, and unstructured data imports.
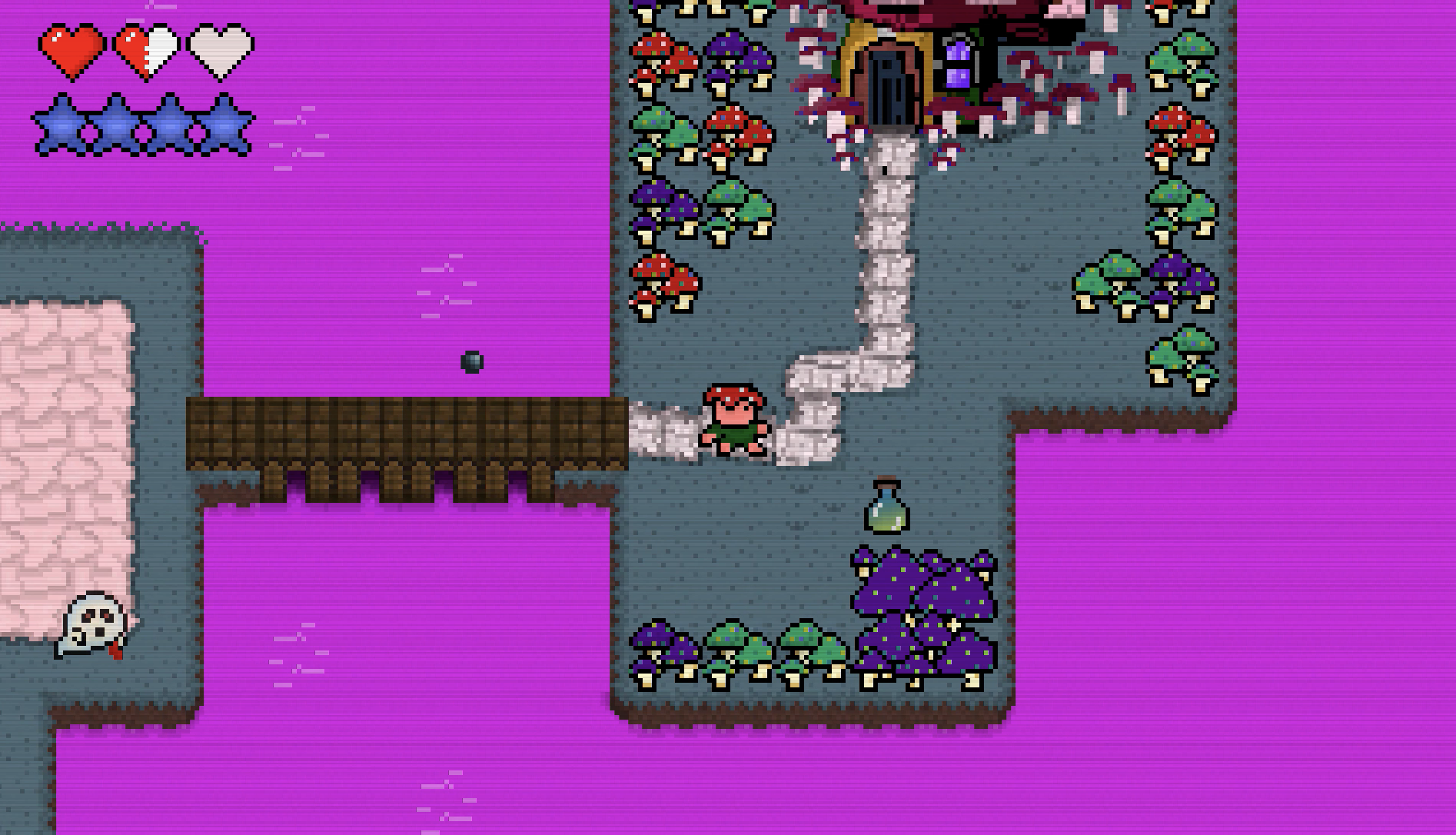
When I started Funguy as a freshman I wanted to truly reflect my creativity and design something of my own no matter how challenging I knew it would be to create from scratch.
I learned how to code in java with zero prior experience. From object oriented programming to designing little 16 bit pixelart characters, I was able to bring the game to life.
You can check out my Dev Instagram for a greater idea on how I created FUNGUY and also check out other projects organized in the highlights. I recently uploaded the code to Github.